Bluejacking vs Bluesnarfing: Exploring Bluetooth Hacking Variations.
Por um escritor misterioso
Descrição
Discover the potential security risks of Bluetooth technology, including various types of attacks like bluejacking, bluesnarfing, bluebugging
Can you get hacked through Bluetooth? - Quora
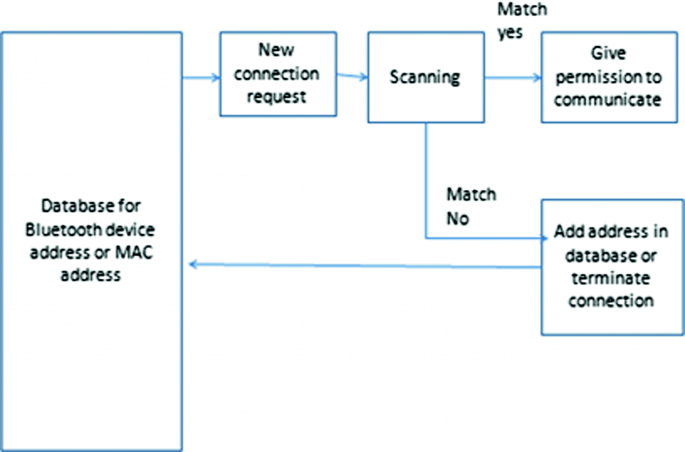
Bluetooth Communication
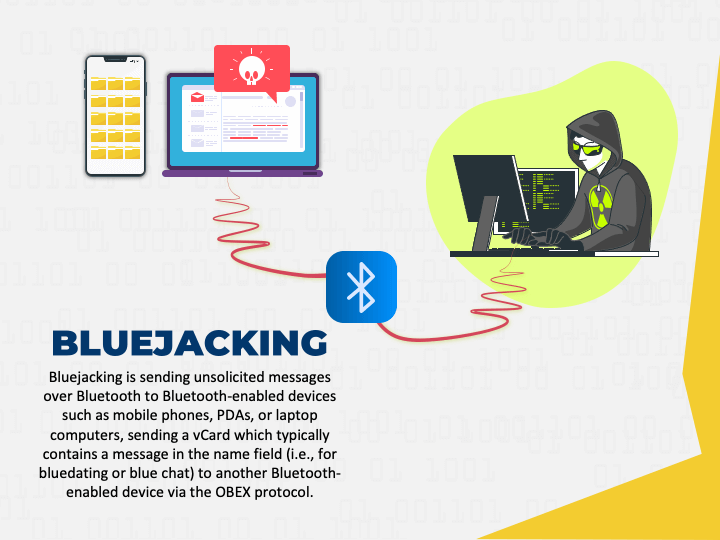
Bluejacking PowerPoint Template - PPT Slides
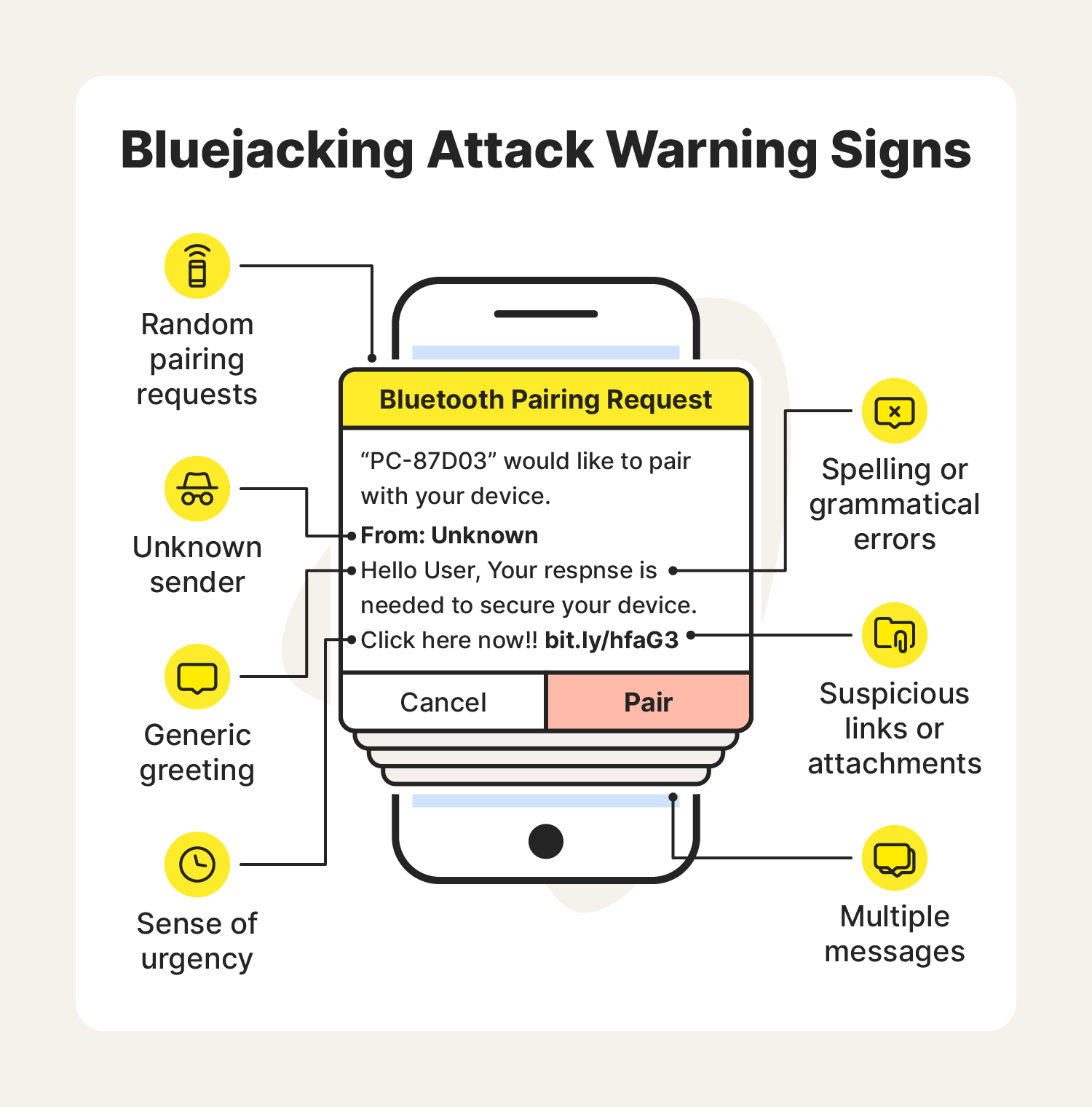
What is bluejacking? Definition + protection tips - Norton

CYBERSECURITY
GitHub - StealthIQ/Bluestrike: Bluestrike: CLI tool to hack Bluetooth devices through speaker jamming, traffic spoofing & device hijacking (In the making)

Bluetooth Security: 5 Ways to prevent Bluetooth attacks

What bluejacking is and how to defend against it - Atlas VPN
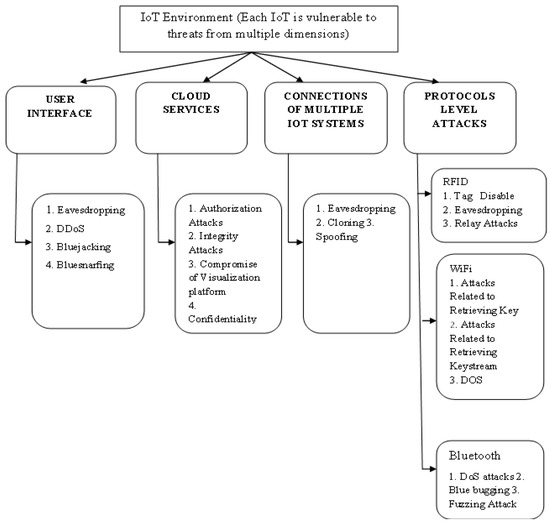
Sensors, Free Full-Text

Bluejacking vs. Bluebugging vs. Bluesnarfing: What's the Difference?
de
por adulto (o preço varia de acordo com o tamanho do grupo)