Cryptojacking - Cryptomining in the browser — ENISA
Por um escritor misterioso
Descrição
The technique of hijacking browsers for mining cryptocurrency (without user consent) is called
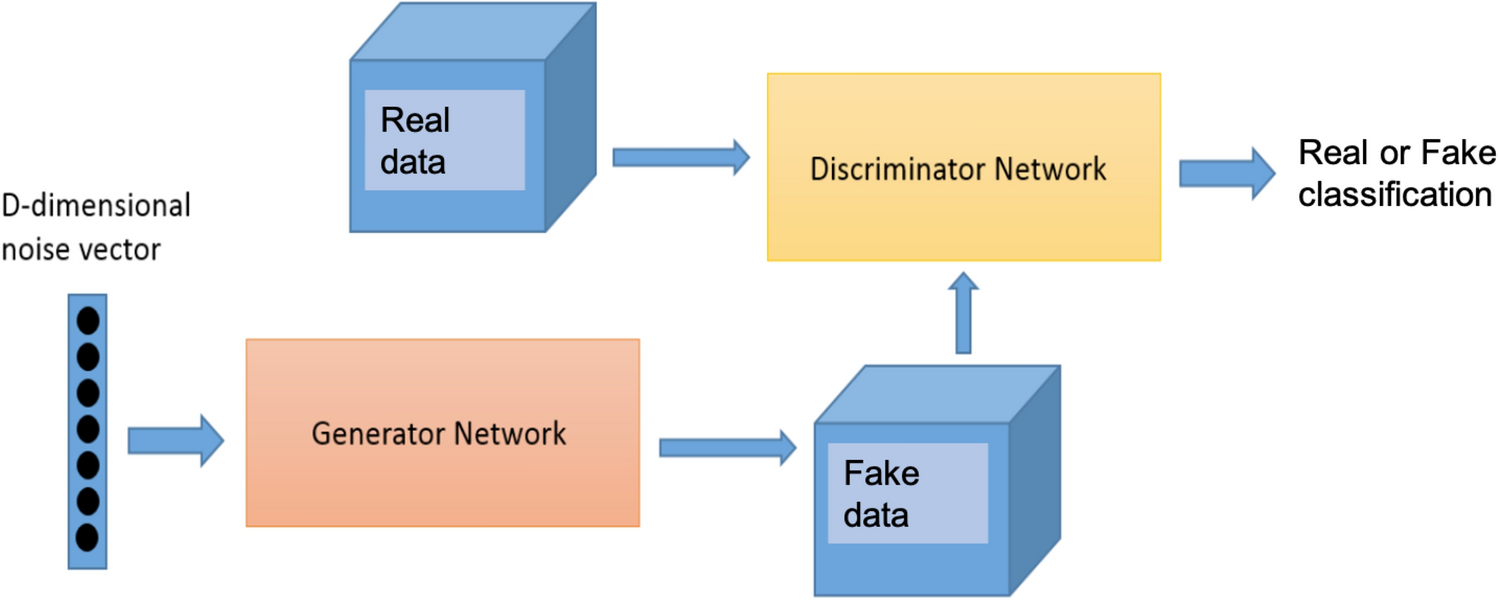
Synthetic flow-based cryptomining attack generation through

MrbMiner cryptojacking campaign linked to Iranian software firm

Reading The ENISA Threat Landscape Report 2018

PDF) Browser Extension for Cryptojacking Malware Detection and

cisco Archives - STL Partners
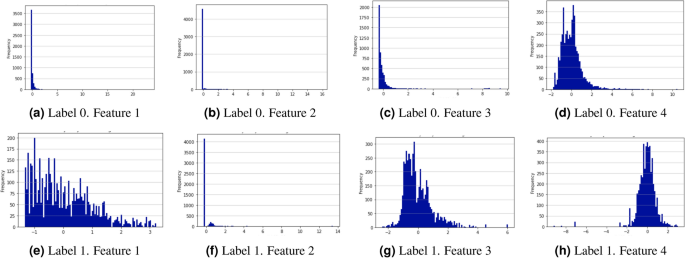
Synthetic flow-based cryptomining attack generation through

What is Cryptojacking? Detection and Preventions Techniques

Cryptojacking

PacNOG 23: Introduction to Crypto Jacking

Unsupervised Anomaly Detectors to Detect Intrusions in the Current

The concept of cryptojacking and how it works?

Cybersecurity Briefing A Recap of Cybersecurity News in
de
por adulto (o preço varia de acordo com o tamanho do grupo)