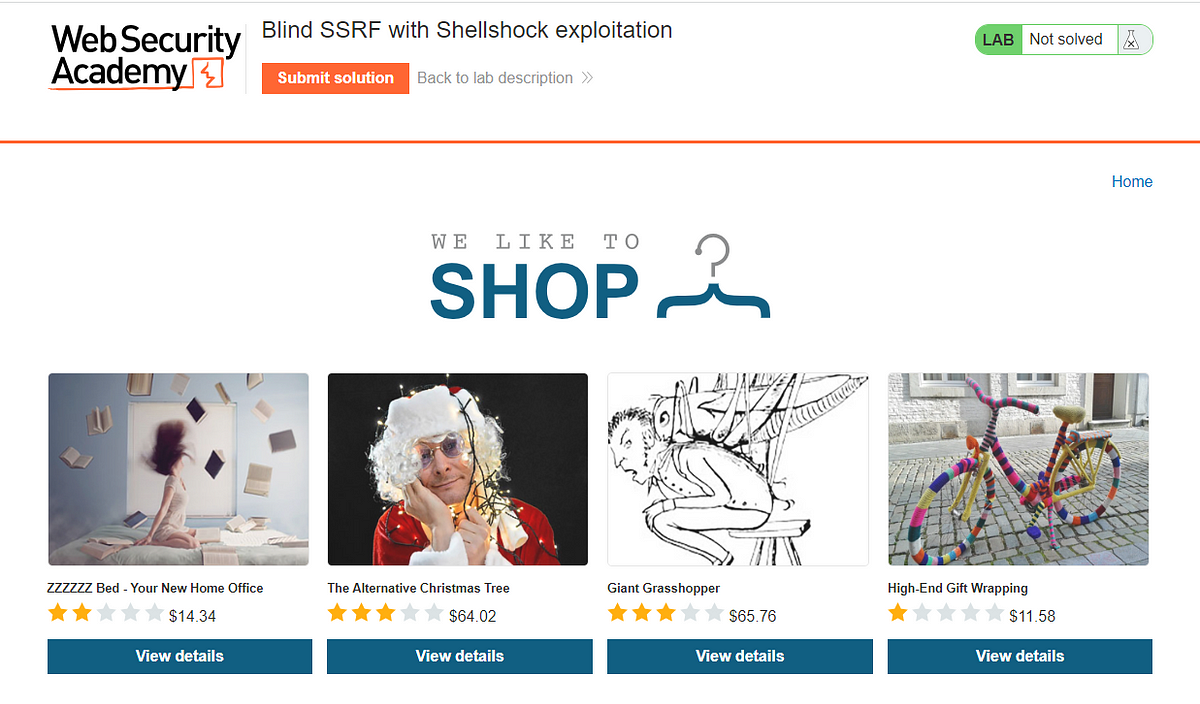
Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Descrição
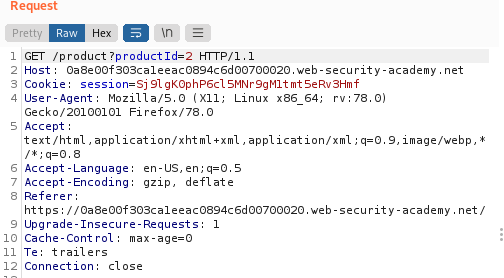
This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this
Solving PortSwigger SSRF Labs - Final Part - ::: re:search + re
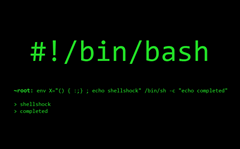
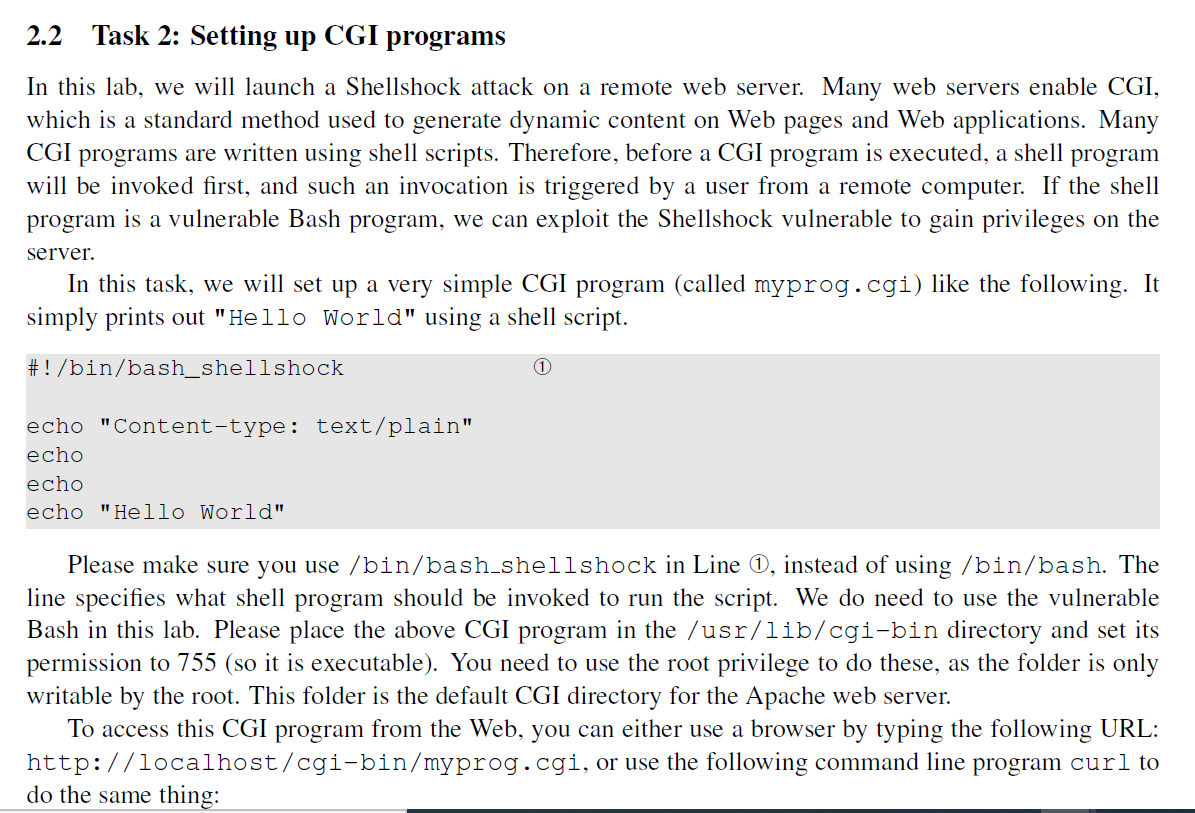
Shellshock Attack Lab
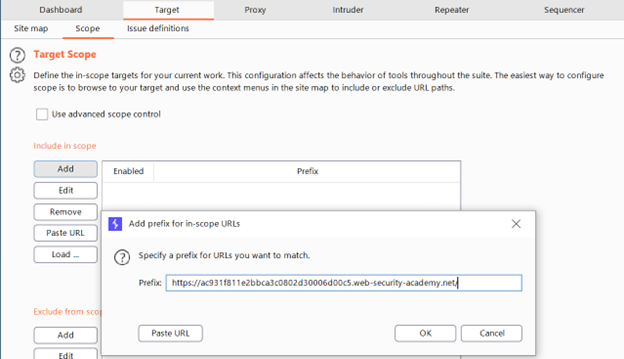
Penetration Testing Step 3 – Blind SSRF attack với hàng độc out-of
A Glossary of Blind SSRF Chains – Assetnote
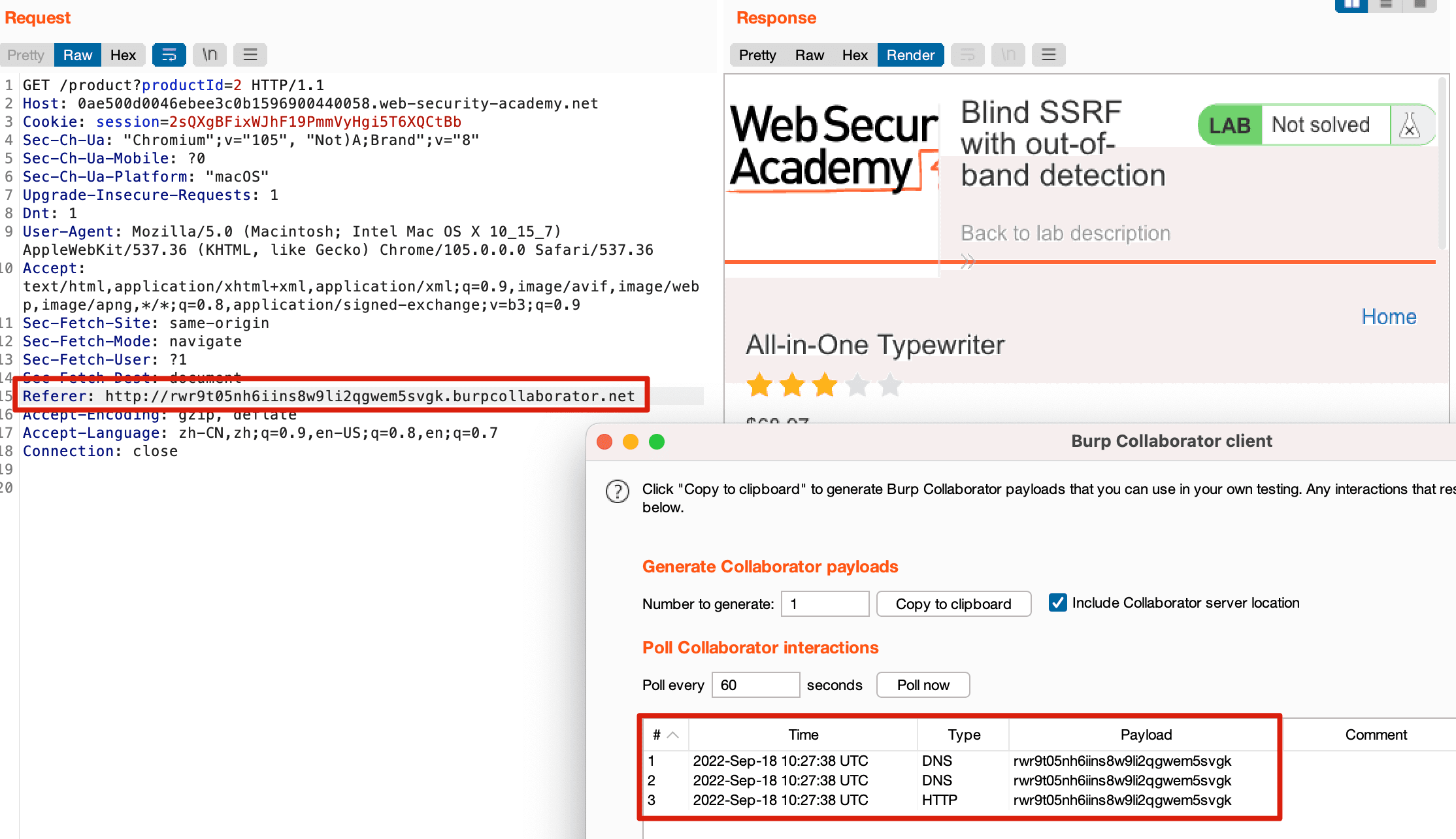
SSRF(服务器跨站请求伪造)基础知识- lca
Server Side Request Forgery · master · pentest-tools
Shivam Rai (@shivam24rai) / X
Solving PortSwigger SSRF Labs - Final Part - ::: re:search + re
Portswigger Web Security Academy Lab: Blind SSRF with

Blind SSRF with Shellshock exploitation (Video solution)

Web Security Academy Series Course
Server Side Request Forgery (SSRF) Zafiyeti Nedir? - BGA Cyber

Web application security in Java > Cydrill Software Security
Solved Readings. Detailed coverage of the Shellshock attack
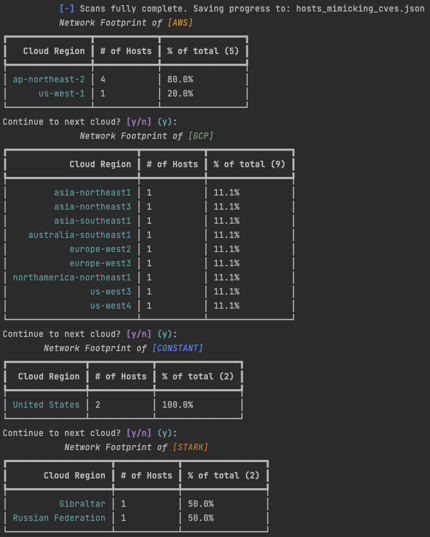
An Attacker's Guide to Evading Honeypots - Part 3
de
por adulto (o preço varia de acordo com o tamanho do grupo)







