Malware analysis Suspicious activity
Por um escritor misterioso
Descrição
Highlight, take notes, and search in the book

Mastering Malware Analysis: A malware analyst's practical guide to combating malicious software, APT, cybercrime, and IoT attacks, 2nd Edition

Malware Incident Response Steps on Windows, and Determining If the
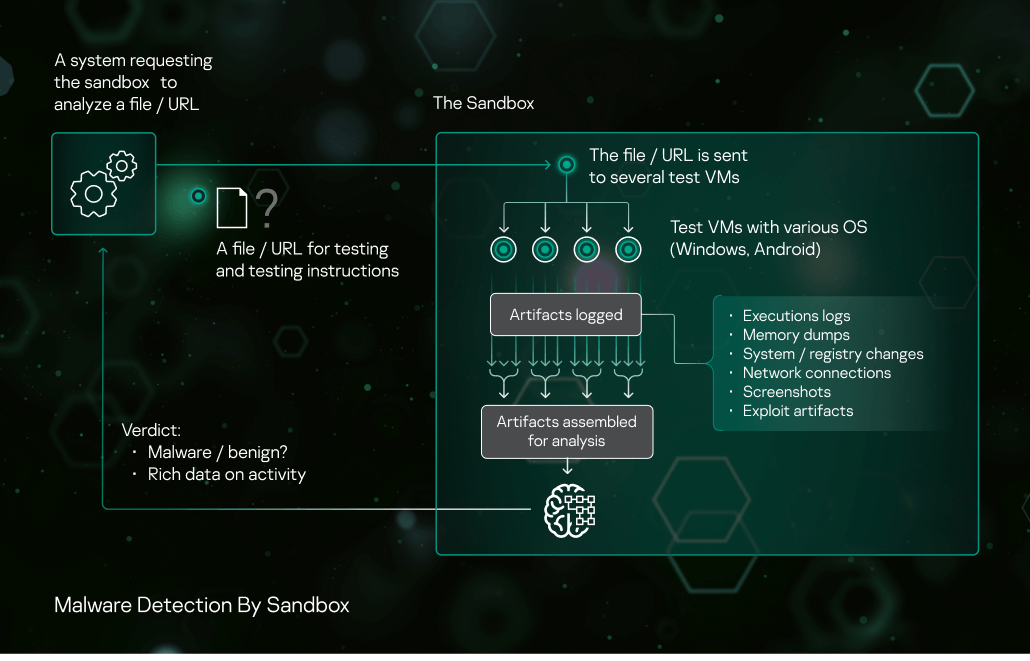
Sandbox Kaspersky

Malware Analysis: Steps & Examples - CrowdStrike
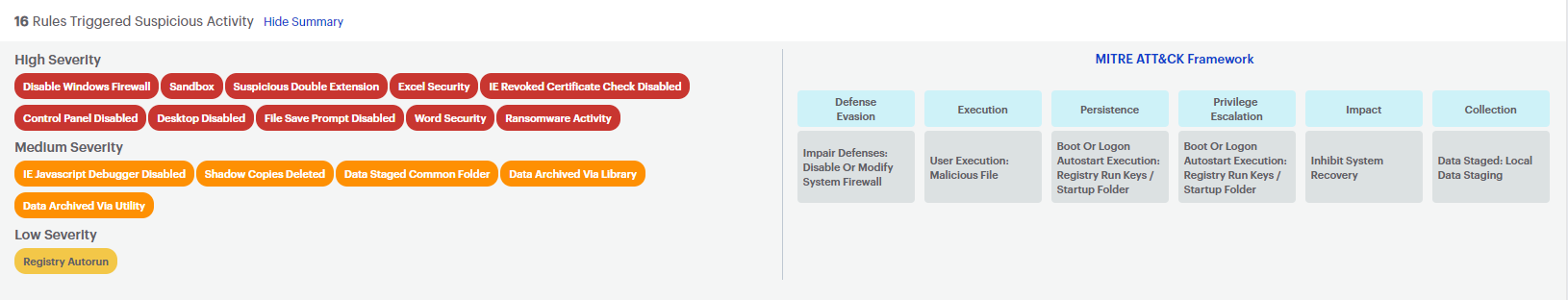
Living Off the Land (LOTL) Attacks: Detect Ransomware Gangs

The Top 10 Malware Analysis Tools

US Cyber Command, DHS-CISA release Russian malware samples tied to
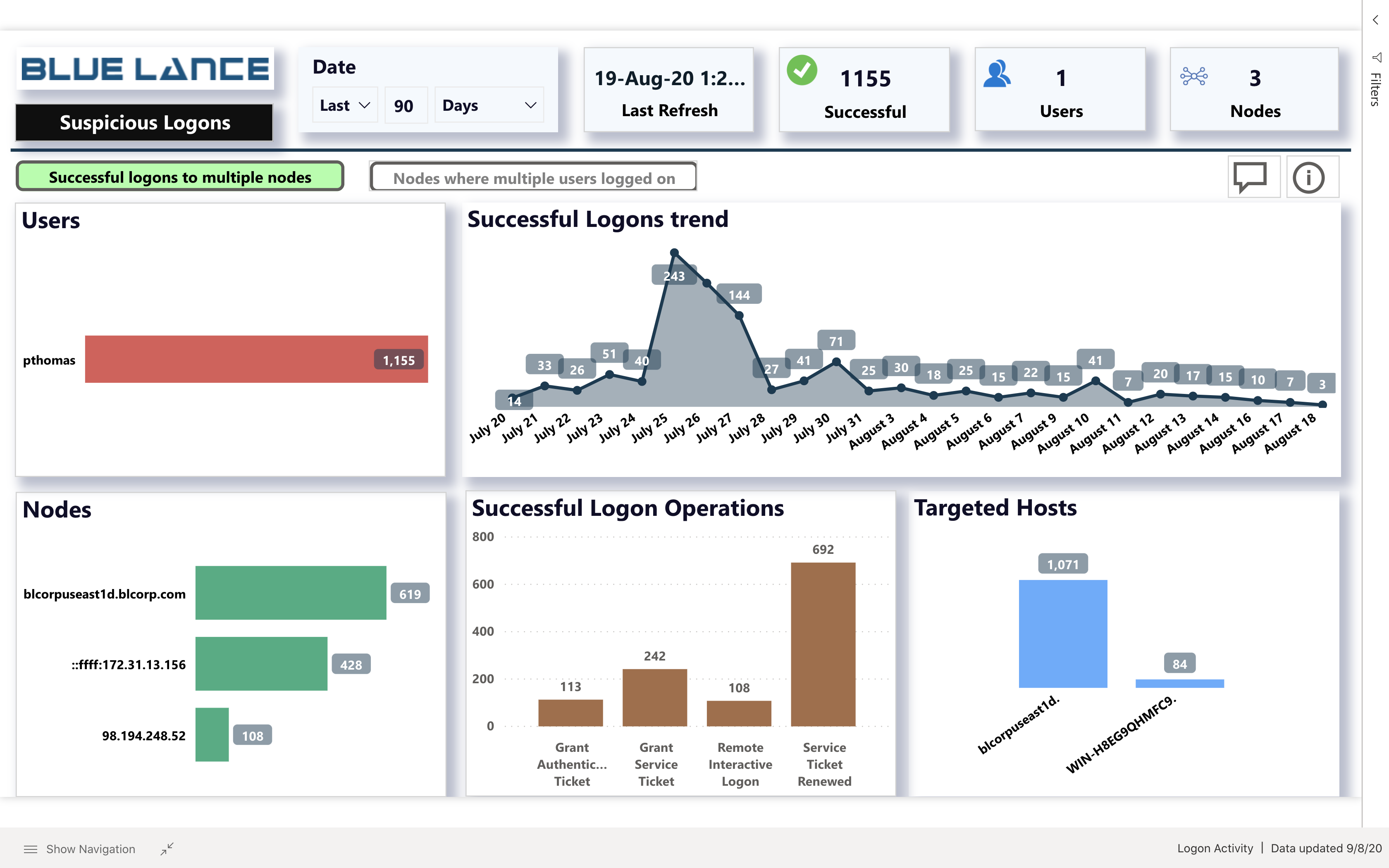
Suspicious Successful Logon Analysis
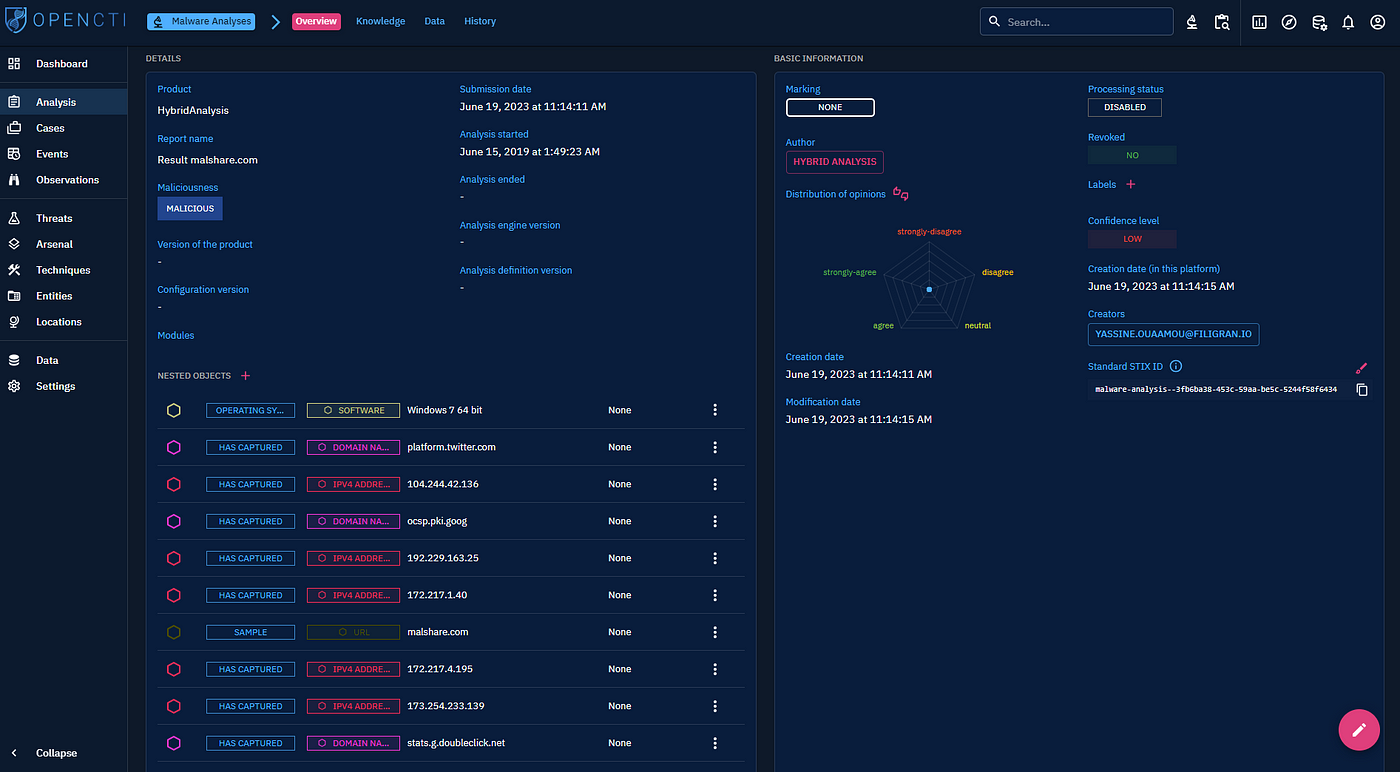
Introducing malware analysis: enhance your cybersecurity triage
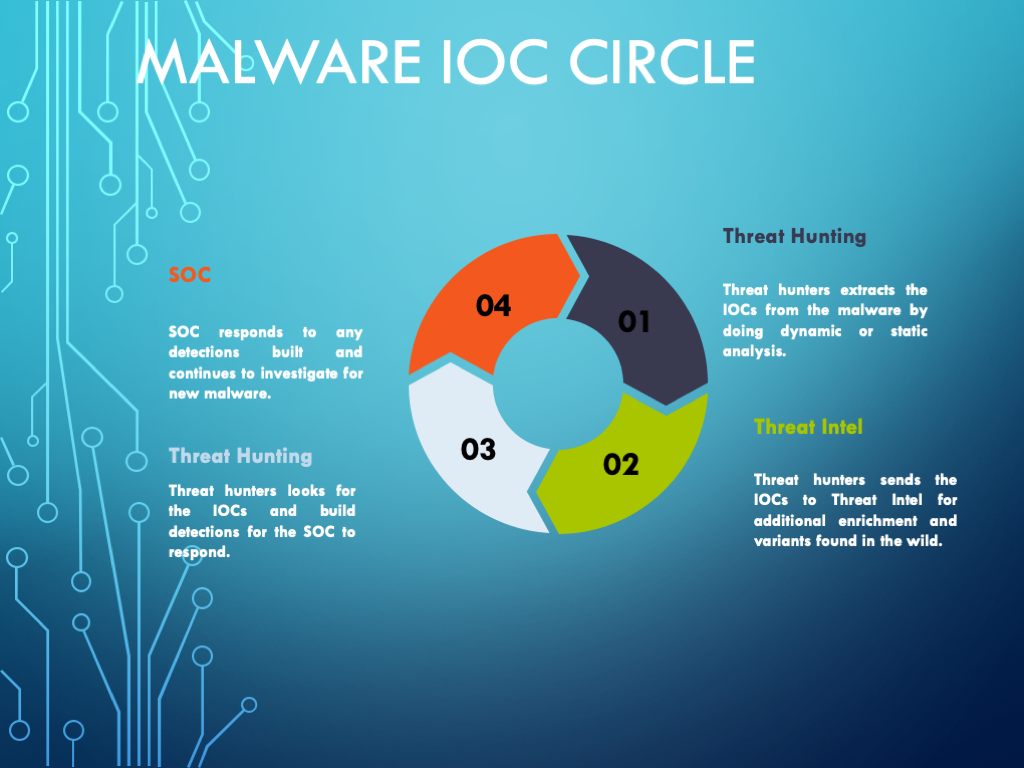
Malware Analysis Framework v1.0

Behavioral blocking and containment: Transforming optics into
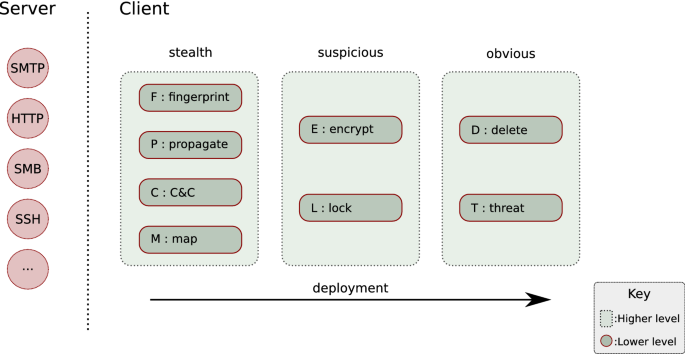
Ransomware deployment methods and analysis: views from a
de
por adulto (o preço varia de acordo com o tamanho do grupo)
:max_bytes(150000):strip_icc()/SL_SEO_112119_AM_IPChickenWings_397-2000-ea1992c08520411c90e113fb5f6cdc0f.jpg)


/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/u/l/wuYu7HTQuyulTYCLYyBQ/2014-10-28-splash6.jpg)
