Reverse engineering Emotet – Our approach to protect GRNET against the trojan
Por um escritor misterioso
Descrição
PE-sieve サイバーセキュリティ情報局
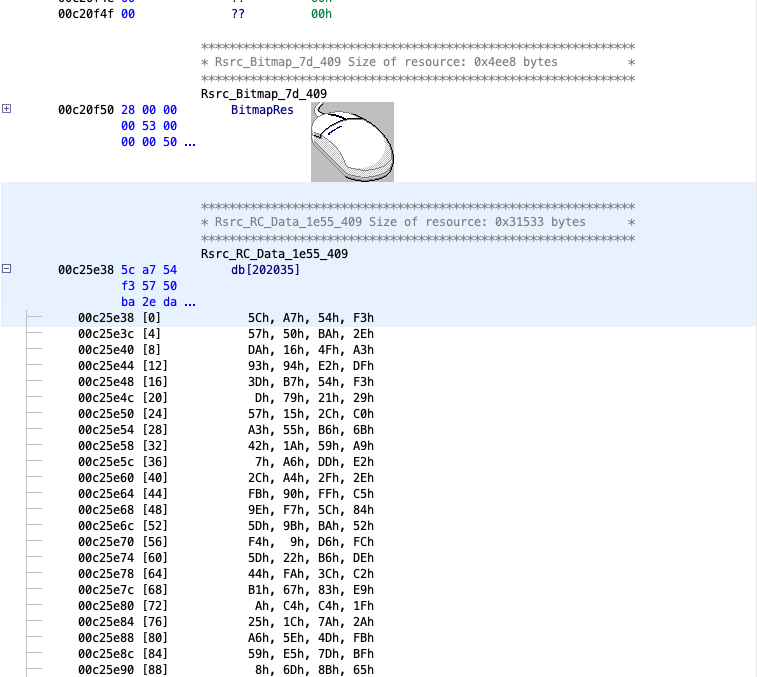
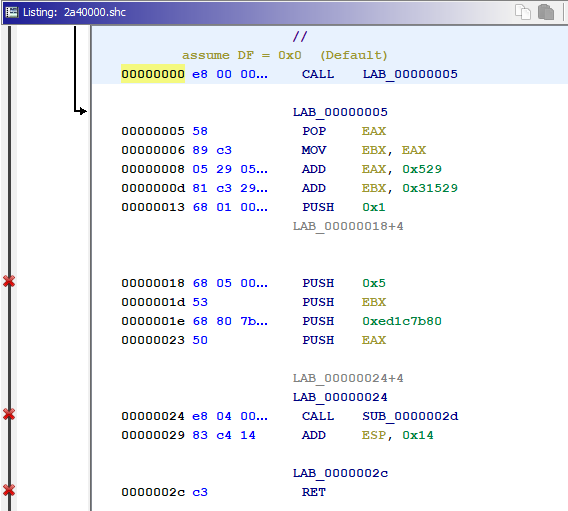
Reverse engineering Emotet – Our approach to protect GRNET against the trojan

Reverse Engineering Emotet. (Behavior and Static Analysis), by Bruno Costa
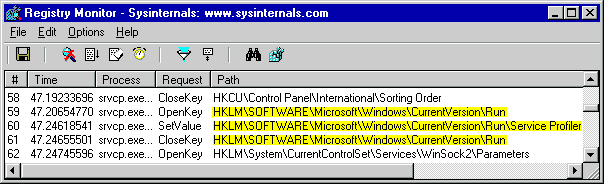
Methodology for Reverse-Engineering Malware
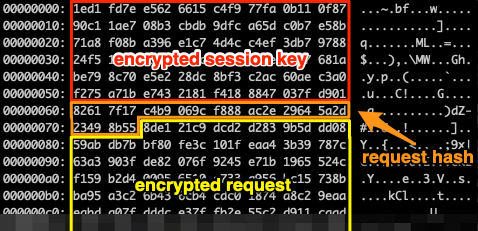
Reverse engineering Emotet – Our approach to protect GRNET against the trojan
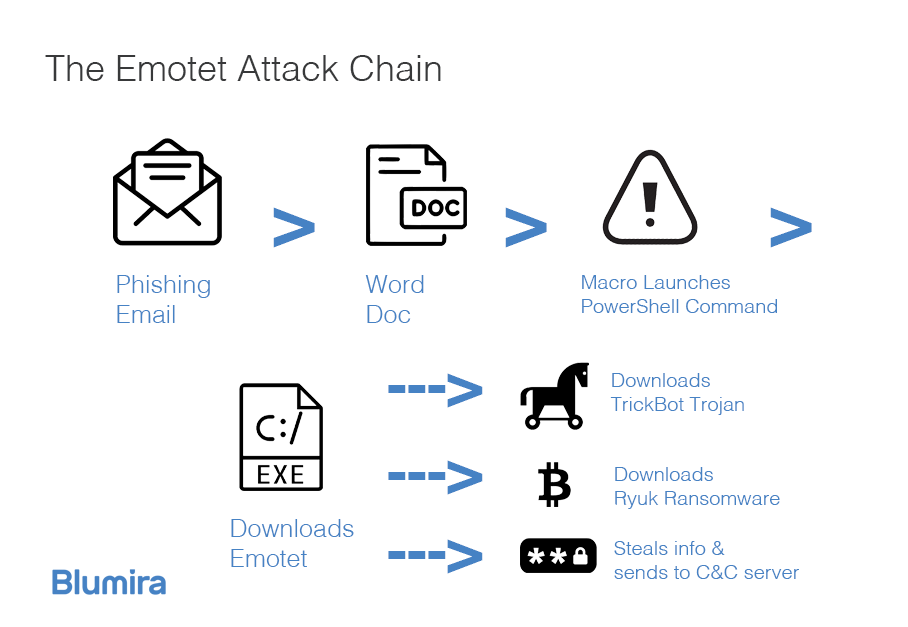
Detect and Protect Against the Return of Emotet Malware
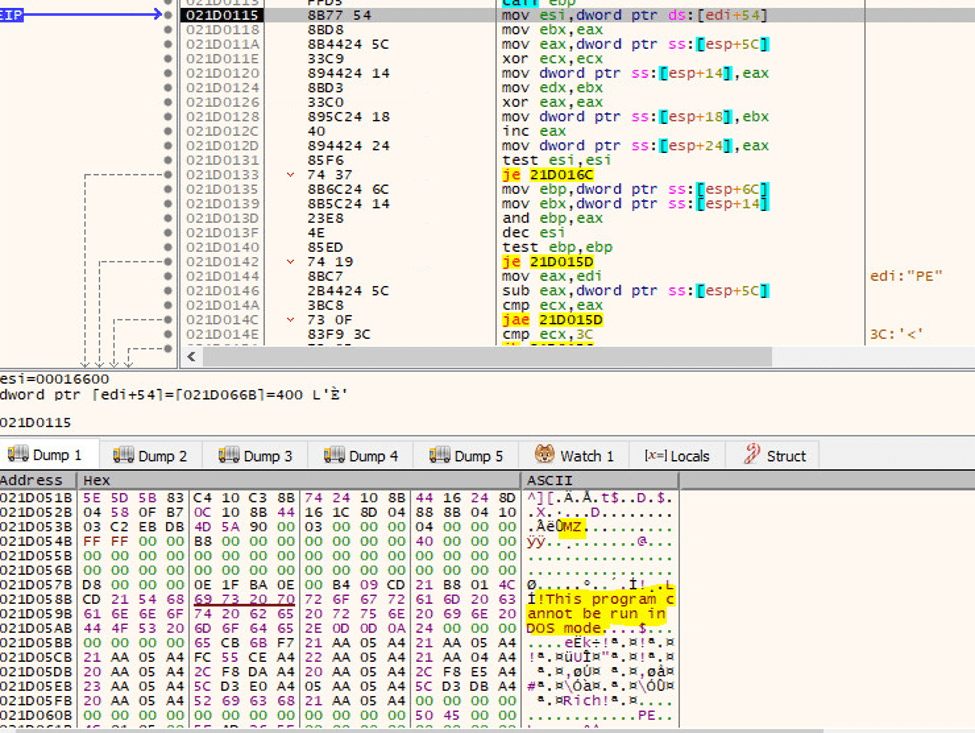
Emotet vs Trump – Deep Dive Analysis of a Killer Info-Stealer - Cynet
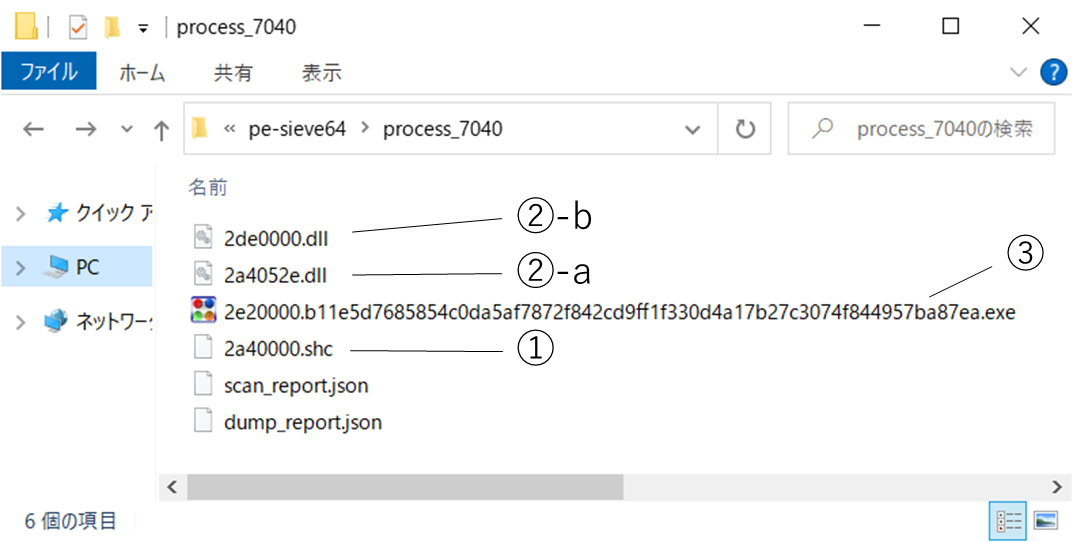
PE-sieve サイバーセキュリティ情報局

GIAC Reverse Engineering Malware (GREM) - Credly

What is Emotet How to best protect yourself
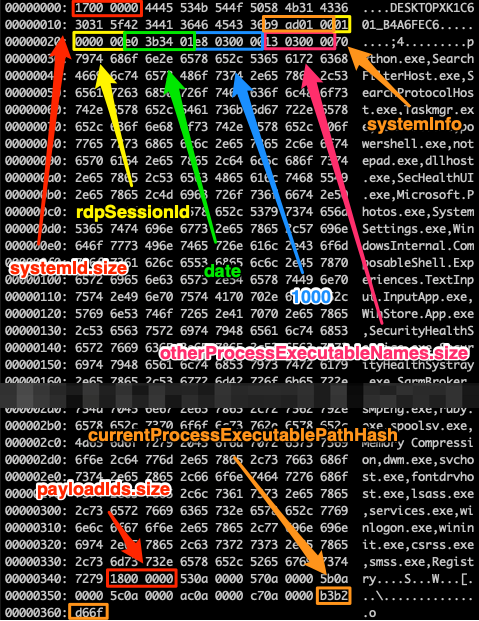
Reverse engineering Emotet – Our approach to protect GRNET against the trojan

Emotet vs Trump – Deep Dive Analysis of a Killer Info-Stealer - Cynet
de
por adulto (o preço varia de acordo com o tamanho do grupo)